hashcat官方从 6.0.0 版本开始,不再接受2500的哈希模式,转为接受新的哈希模式 22000
如果仍旧使用-m 2500则会遇到报错
The plugin 2500 is deprecated and was replaced with plugin 22000. For more details, please read: https://hashcat.net/forum/thread-10253.html
解决方法之一就是将不再受支持的hccapx格式转换为hc22000格式
hccapx的结构
用16进制编辑器打开可以看到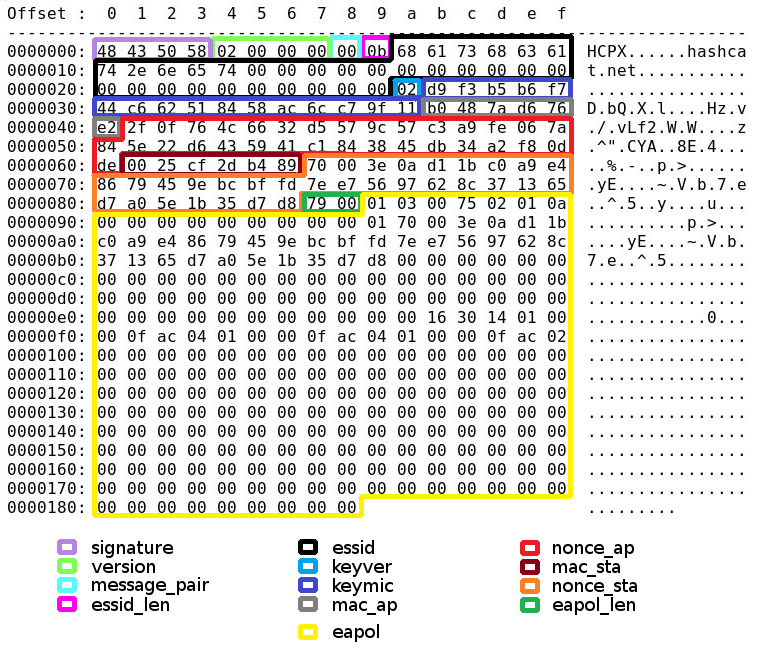
hc22000的结构
本质上是将原本hccapx格式中的字段重新排列,然后以文本形式而非16进制呈现
重新排列的顺序为
PROTOCOL*TYPE*PMKID/MIC*MACAP*MACCLIENT*ESSID*ANONCE*EAPOL*MESSAGEPAIR
下面一个将2500模式下hccapx格式转为最新的hc2200的小程序,源码来自sleshep
import sys
import os
import struct
def main():
if len(sys.argv) != 2:
print("Usage: python convert_hccapx_to_22000.py <input_hccapx_file>")
sys.exit(1)
input_file = sys.argv[1]
if not os.path.isfile(input_file):
print(f"Error: File '{input_file}' does not exist.")
sys.exit(1)
with open(input_file, "rb") as f:
data = f.read()
def get_data(fmt, data):
result = struct.unpack(fmt, data)
# unpack the (som,) to som
if isinstance(result, tuple) and len(result) == 1:
result = result[0]
return result
"""
Field name Offsets (hex) Offsets (dec) Field description
signature 0x00 to 0x03 0 to 3 the signature (file magic) of .hccapx files, it is always the string HCPX
version 0x04 to 0x07 4 to 7 the version number of the .hccapx file format
message_pair 0x08 8 possible values range from 0 to 5 or 128 to 133 (see message_pair table below) 1
essid_len 0x09 9 the length of the network name (ESSID)
essid 0x0a to 0x29 10 to 41 the network name (ESSID)
keyver 0x2a 42 set to 1 if WPA is used, other values (preferably 2) means WPA2
keymic 0x2b to 0x3a 43 to 58 the actual hash value (MD5 for WPA, SHA1 for WPA2) truncated to 128 bit (16 bytes)
mac_ap 0x3b to 0x40 59 to 64 the mac address of the access point (BSSID)
nonce_ap 0x41 to 0x60 65 to 96 nonce (random salt) generated by the access point
mac_sta 0x61 to 0x66 97 to 102 the mac address of the client connecting to the access point
nonce_sta 0x67 to 0x86 103 to 134 nonce (random salt) generated by the client connecting to the access point
eapol_len 0x87 to 0x88 135 to 136 the length of the EAPOL
eapol 0x89 to 0x188 137 to 392 the EAPOL (max 256 bytes)
"""
signature: str = get_data('4s', data[0:4]) # type:ignore
if signature != b'HCPX':
print(f"Error: Invalid hccapx file.signature is {signature}")
sys.exit(1)
version: int = get_data('I', data[4:8]) # type:ignore
message_pair: int = get_data('B', data[8:9]) # type:ignore
essid_len: int = get_data('B', data[9:10]) # type:ignore
essid: bytes = get_data(
f'{essid_len}s', data[10:10+essid_len]) # type:ignore
keyver: int = get_data('B', data[42:43]) # type:ignore
keymic: bytes = get_data('16s', data[43:59]) # type:ignore
mac_ap: bytes = get_data('6s', data[59:65]) # type:ignore
nonce_ap: bytes = get_data('32s', data[65:97]) # type:ignore
mac_sta: bytes = get_data('6s', data[97:103]) # type:ignore
nonce_sta: bytes = get_data('32s', data[103:135]) # type:ignore
eapol_len: int = get_data('H', data[135:137]) # type:ignore
eapol: bytes = get_data(f'{eapol_len}s', data[137:137+eapol_len]) # type:ignore
"""
For developers
The new hash format 22000 in detail:
Code:
PROTOCOL*TYPE*PMKID/MIC*MACAP*MACCLIENT*ESSID*ANONCE*EAPOL*MESSAGEPAIR
PROTOCOL = Fixed string "WPA"
TYPE = 01 for PMKID, 02 for EAPOL
PMKID/MIC = PMKID if TYPE=01, MIC if TYPE=02
MACAP = MAC of AP
MACCLIENT = MAC of CLIENT
ESSID = network name (ESSID) in HEX
ANONCE = ANONCE
EAPOL = EAPOL (SNONCE is in here)
MESSAGEPAIR = Bitmask:
0: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
1: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
2: MP info (https://hashcat.net/wiki/doku.php?id=hccapx)
3: x (unused)
4: ap-less attack (set to 1) - no nonce-error-corrections necessary
5: LE router detected (set to 1) - nonce-error-corrections only for LE necessary
6: BE router detected (set to 1) - nonce-error-corrections only for BE necessary
7: not replaycount checked (set to 1) - replaycount not checked, nonce-error-corrections definitely necessary
"""
# Construct hashcat 22000 format string
protocol = "WPA"
pmkid_mic = keymic.hex()
type = "02"
if keyver == 1:
raise Exception("version 2 file not supported")
mac_ap_hex = mac_ap.hex()
mac_client_hex = mac_sta.hex()
essid_hex = essid.hex()
nonce_ap_hex = nonce_ap.hex()
eapol_hex = eapol.hex()
message_pair_hex = f"{message_pair:02x}"
hc22000 = f"{protocol}*{type}*{pmkid_mic}*{mac_ap_hex}*{mac_client_hex}*{essid_hex}*{nonce_ap_hex}*{eapol_hex}*{message_pair_hex}"
print(hc22000)
def change_extension(inputfile, new_extension=".hc22000"):
"""
更改文件的后缀名
:param inputfile: 输入文件的路径
:param new_extension: 新的后缀名(例如 ".txt", ".csv")
:return: 返回新的文件名
"""
# 获取文件名(不含路径)和目录
base_name = os.path.basename(inputfile) # 获取文件名(含后缀)
dir_name = os.path.dirname(inputfile) # 获取目录路径
# 分离文件名和后缀
name, _ = os.path.splitext(base_name) # 分离文件名和后缀
# 构建新的文件名
new_filename = name + new_extension
# 如果目录不为空,拼接目录和新的文件名
if dir_name:
new_filepath = os.path.join(dir_name, new_filename)
else:
new_filepath = new_filename
return new_filepath
outputfile = change_extension(input_file)
with open(outputfile, 'w') as outfile:
outfile.writelines(hc22000)
if __name__ == "__main__":
main()
顺便附带两条常用的掩码模式破解语句
8位小写字母
hashcat -a 3 -m 22000 dNKc.hc22000 ?l?l?l?l?l?l?l?l -o dump.txt
8位小写字母数字混合
hashcat -a 3 -m 22000 dNKc.hc22000 -1 ?l?d ?1?1?1?1?1?1?1?1 -o dump.txt
ref : https://hashcat.net/wiki/doku.php?id=hccapx
ref : https://hashcat.net/wiki/doku.php?id=cracking_wpawpa2#expected_file_format